Sabado, Abril 30, 2011
III. Written Case Analysis Grading Rubric
From: www.newbedford.k12.ma.us/.../Case%20Analysis%20Grading%20Rubric.doc
Score ORGANIZATION: Logical sequencing; transitions
4 The presentation follows the required format. A forward progression of ideas with smooth and clear transitions from one
part of the Case Analysis to the next is evident. The listener can effortlessly follow the piece.
3 The presentation follows the format. The presentation does contain all parts of the Case Analysis, yet the transitions from
one section to the next are not always clear.
2 The format of the presentation is not clearly followed. Transitions from one element of the Case Analysis to the next are
poorly organized and are confusing for the listener to follow.
1 Presentation format is lacking. The progression of ideas is difficult or impossible to follow.
DETAILS and CONTENT: Appropriate to purpose, consistently maintained; depth or elaboration.
6 The presentation offers an accurate and complete discussion of the Background Facts of the case; the Question to the Court
accurately presents the issue; the Decision of the Court and rule of law are accurately and completely discussed. The presenta
tion shows depth by the use of accurate and pertinent details.
4 The presentation offers a discussion of the Background Facts of the case; the Question to the Court accurately presents the
issue; the Decision of the Court and rule of law are discussed. A flaw exists in one of the elements of the case analysis. Some
details and discussion beyond the slides add some depth to the presentation.
2 The presentation has a 2 or more flaws in the discussion of the Background Facts, the Question to the Court (issue); and the
Decision of the Court and Rule of Law. The presentation lacks depth. Few, if any, ideas or details are developed. Student(s)
basically read the slides.
1 The presentation has a many flaws in the discussion of the Background Facts, the Question to the Court (issue); and the Deci
sion of the Court and Rule of Law. The presentation lacks depth. Details are inaccurate or lacking. Students read the slides.
STUDENT LED DISCUSSION & PRESENTATION: Proper use of PowerPoint as a tool; student led presentation and discussion of the case.
4 Student(s) describe elements of the case without constantly reading the slide and can expound upon each element and
respond to questions with confidence. (All group members participate)
3 Student(s) describes elements of the case with reference to the slide and can expound upon each element and respond to ques
tions with prompting. (Some all group members participate)
2 Student(s) present elements of the case by simply reading the slide. There is difficulty in elaboration and responding to questions.
(Few group members participate)
1 Student(s) presentation of the elements of the case is limited to reading the slide; student(s) are unable to expound upon
each element or respond to questions. (ONE group member participates)
SLIDE SHOW & POWERPOINT: Use of technology
4 Slides are neat, no spelling errors; use of graphics and sounds enhances presentation; size of print and colors enable the slides to
be easily read around the classroom.
3 Slides are neat, some spelling errors; some use of graphics and sounds; size of print and colors enable the slides to be read around
the classroom.
2 Slides are neat, a number of spelling errors; little use or inappropriate use of graphics and sounds; size of print and colors make it
difficult to read the slides around the classroom.
1 Many spelling errors; inappropriate or no use of graphics and sounds; size of print and colors make it difficult to read the slides
around the classroom.
II. Tips for Effective Classroom Management
According to Fred Jones' Positive Classroom Discipline, "The most widespread management technique at home and in the classroom is nag, nag, nag."
It's also probably the least effective.
How can you avoid making that technique your own and create a "climate for learning"? This week, Education World looks to the experts -- teachers who've "been there, done that" and found a better way -- for answers.
Howard Miller, Associate Professor of Education at Lincoln University (Jefferson City, Missouri) suggests 12 steps teachers can take at the beginning of the year to promote effective classroom management.
1. Develop a set of written expectation you can live with and enforce.
2. Be consistent. Be consistent. Be consistent.
3. Be patient with yourself and with your students.
4. Make parents your allies. Call early and often. Use the word "concerned." When
communicating a concern, be specific and descriptive.
5. Don't talk too much. Use the first 15 minutes of class for lectures or presentations, then
get the kids working.
6. Break the class period into two or three different activities. Be sure each activity segues
smoothly into the next.
7. Begin at the very beginning of each class period and end at the very end.
8. Don't roll call. Take the roll with your seating chart while students are working.
9. Keep all students actively involved. For example, while a student does a presentation,
involve the other students in evaluating it.
10. Discipline individual students quietly and privately. Never engage in a disciplinary
conversation across the room.
11. Keep your sense of perspective and your sense of humor.
12. Know when to ask for help.
I. Summary of R.A. 8792 (E Commerce Law)
From: From: http://ross17.blogspot.com/2009/09/summary-of-ra-8792-e-commerce-law_15.html
With the Philippines relaxed stock market listing rules plus a proposed vibrant investment priorities program in place, Filipinos here and abroad, and its foreign partners, have something to look forward for.
Here are the salient features of Republic Act 8792:
It gives legal recognition of electronic data messages, electronic documents, and electronic signatures. (section 6 to 13)
Allows the formation of contracts in electronic form. (section 16)
Makes banking transactions done through ATM switching networks absolute once consummated. (section 16)
Parties are given the right to choose the type and level of security methods that suit their needs. (section 24)
Provides the mandate for the electronic implementation of transport documents to facilitate carriage of goods. This includes documents such as, but not limited to, multi-modal, airport, road, rail, inland waterway, courier, post receipts, transport documents issued by freight forwarders, marine/ocean bill of lading, non-negotiable seaway bill, charter party bill of lading. (section 25 and 26)
Mandates the government to have the capability to do e-commerce within 2 years or before June 19, 2002. (section 27)
Mandates RPWeb to be implemented. RPWeb is a strategy that intends to connect all government offices to the Internet and provide universal access to the general public. The Department of Transportation and Communications, National Telecommunications Commission, and NationalComputer Center will come up with policies and rules that shall lead to substantial reduction of costs of telecommunication and Internet facilities to ensure the implementation of RPWeb. (section 28)
Made cable, broadcast, and wireless physical infrastructure within the activity of telecommunications. (section 28)
Empowers the Department of Trade and Industry to supervise the development of e-commerce in the country. It can also come up with policies and regulations, when needed, to facilitate the growth of e-commerce. (section 29)
Provided guidelines as to when a service provider can be liable. (section 30)
Authorities and parties with the legal right can only gain access to electronic documents, electronic data messages, and electronic signatures. For confidentiality purposes, it shall not share or convey to any other person. (section 31 and 32)
Hacking or cracking, refers to unauthorized access including the introduction of computer viruses, is punishable by a fine from 100 thousand to maximum commensurating to the damage. With imprisonment from 6 months to 3 years. (section 33)
Piracy through the use of telecommunication networks, such as the Internet, that infringes intellectual property rights is punishable. The penalties are the same as hacking. (section 33)
All existing laws such as the Consumer Act of the Philippinesalso applies to e-commerce transactions. (section 33) Anyone who uses the Internet, computer, cellular phone, and other IT-enabled devices has the duty to know RA8792. As the old saying goes, "Ignorance of the law doesn't excuse anyone."
There were several hacking/cracking incidents that took place in the past five years. I am worried that these people behind the hacking attempts are completely ignoring RA8792 or The E-Commerce Law. In one of my public speaking engagements, I was asked how come there are still so many hacking attempts even now that we have a law. Is it unenforceable?
I fear that as e-commerce takes off in the government and private sector, the moment we run to law enforcers in times of trouble, they will not be able to help us.
The law enforcement agencies such as the National Bureau of Investigation and Philippine National Police are continuously beefing up their skills. It is sad to note however that they have not received any form of funding for their training and cybercrime equipment. Whatever they have right now are donated by foreign governments in the form of training and equipment. Despite limited resources, the conviction of the first Filipino hacker under Republic Act 8792 puts high marks on our enforcement of the E-Commerce Law.
The business community and Internet users must contribute and work with government to take action on this. It is not the Cybercrime bill that is important today, giving appropriate funding for cybercrime enforcement is, that will allow the creation of cybercrime helpdesks all over the country.
In addition, it requires vigilance from the Internet community as well. If you know of someone that has made these hacking actions, report them. It is the duty of every Filipino to report these crimes. They can contact the Cyber Crime Anti Fraud Division of the National Bureau of Investigation at Taft Ave., Manila, phone number (632) 5254093 and look for Director Reynaldo Wycoco or Atty. Elfren Meneses, Jr. Those who became victims as well should report it and not just ignore it, change the site, and move on. If this is the attitude that site owners will show, unlawful actions such as this, regardless of best or worst intention, will never cease. The web hosting, Internet Service Provider, phone companies should extend their best cooperation as well to facilitate efficient investigation in this regard.
More importantly, what the hackers should realize that just because they were not caught now, does not mean they are already off the hook. What they are only doing is accumulate offenses. One day, the hand of the law will reach them. Once that happens, all of these offenses can be combined into a one big case that can put them to jail longer than they think. Even if the owners of the sites that they were able to hack decide not to pursue a case against them, it does not mean they no longer have a liability. The hacking/cracking/piracy provision of the E-Commerce Law makes such acts as criminal offenses in nature, therefore what can only be waived, should the companies decide not to sue them, is the civil liability (monetary damages) and the criminal liability will still be pursued by the state.
I hope that publications can play a role in sparking vigilance among Internet users of this country and the world against acts of hacking/cracking/piracy. The act of hacking should never be glamorized and even make these people who commits these acts as heroes. It may send a wrong signal that our younger Internet generation might misunderstand.
These people are seeing that they're getting the media mileage and attention that they long for and see it like a merit/badge of their hacking accomplishment. Being published, talked about, is I'm very sure, a big deal for some of these guys.
I hope to see the computer publications as a medium in making the Internet users vigilant and not scared/wary of these hackers. Perhaps feature articles on how the NBI, ISPs, phone companies, National Security Council, handle these incidents.
Hacking, cracking, piracy is a crime under RA8792. The iron hand of the law must be fully enforced or else this can propagate further and cause irreparable damage to the Philippine Internet industry as a whole. The increase number of hacking incidents these past few weeks is already alarming. Worst, these people seems to be enjoying it and not even bothered with the consequences.
Republic Act 8792, was signed into law last June 14, 2000. It is a landmark legislation in the history of the Philippines. Not only has this bill made the country a legitimate player in the global marketplace. The Philippine Internet community has played a major role in pushing for its passage. The law took effect last June 19, 2000.
With the Philippines relaxed stock market listing rules plus a proposed vibrant investment priorities program in place, Filipinos here and abroad, and its foreign partners, have something to look forward for.
Here are the salient features of Republic Act 8792:
It gives legal recognition of electronic data messages, electronic documents, and electronic signatures. (section 6 to 13)
Allows the formation of contracts in electronic form. (section 16)
Makes banking transactions done through ATM switching networks absolute once consummated. (section 16)
Parties are given the right to choose the type and level of security methods that suit their needs. (section 24)
Provides the mandate for the electronic implementation of transport documents to facilitate carriage of goods. This includes documents such as, but not limited to, multi-modal, airport, road, rail, inland waterway, courier, post receipts, transport documents issued by freight forwarders, marine/ocean bill of lading, non-negotiable seaway bill, charter party bill of lading. (section 25 and 26)
Mandates the government to have the capability to do e-commerce within 2 years or before June 19, 2002. (section 27)
Mandates RPWeb to be implemented. RPWeb is a strategy that intends to connect all government offices to the Internet and provide universal access to the general public. The Department of Transportation and Communications, National Telecommunications Commission, and NationalComputer Center will come up with policies and rules that shall lead to substantial reduction of costs of telecommunication and Internet facilities to ensure the implementation of RPWeb. (section 28)
Made cable, broadcast, and wireless physical infrastructure within the activity of telecommunications. (section 28)
Empowers the Department of Trade and Industry to supervise the development of e-commerce in the country. It can also come up with policies and regulations, when needed, to facilitate the growth of e-commerce. (section 29)
Provided guidelines as to when a service provider can be liable. (section 30)
Authorities and parties with the legal right can only gain access to electronic documents, electronic data messages, and electronic signatures. For confidentiality purposes, it shall not share or convey to any other person. (section 31 and 32)
Hacking or cracking, refers to unauthorized access including the introduction of computer viruses, is punishable by a fine from 100 thousand to maximum commensurating to the damage. With imprisonment from 6 months to 3 years. (section 33)
Piracy through the use of telecommunication networks, such as the Internet, that infringes intellectual property rights is punishable. The penalties are the same as hacking. (section 33)
All existing laws such as the Consumer Act of the Philippinesalso applies to e-commerce transactions. (section 33) Anyone who uses the Internet, computer, cellular phone, and other IT-enabled devices has the duty to know RA8792. As the old saying goes, "Ignorance of the law doesn't excuse anyone."
There were several hacking/cracking incidents that took place in the past five years. I am worried that these people behind the hacking attempts are completely ignoring RA8792 or The E-Commerce Law. In one of my public speaking engagements, I was asked how come there are still so many hacking attempts even now that we have a law. Is it unenforceable?
I fear that as e-commerce takes off in the government and private sector, the moment we run to law enforcers in times of trouble, they will not be able to help us.
The law enforcement agencies such as the National Bureau of Investigation and Philippine National Police are continuously beefing up their skills. It is sad to note however that they have not received any form of funding for their training and cybercrime equipment. Whatever they have right now are donated by foreign governments in the form of training and equipment. Despite limited resources, the conviction of the first Filipino hacker under Republic Act 8792 puts high marks on our enforcement of the E-Commerce Law.
The business community and Internet users must contribute and work with government to take action on this. It is not the Cybercrime bill that is important today, giving appropriate funding for cybercrime enforcement is, that will allow the creation of cybercrime helpdesks all over the country.
In addition, it requires vigilance from the Internet community as well. If you know of someone that has made these hacking actions, report them. It is the duty of every Filipino to report these crimes. They can contact the Cyber Crime Anti Fraud Division of the National Bureau of Investigation at Taft Ave., Manila, phone number (632) 5254093 and look for Director Reynaldo Wycoco or Atty. Elfren Meneses, Jr. Those who became victims as well should report it and not just ignore it, change the site, and move on. If this is the attitude that site owners will show, unlawful actions such as this, regardless of best or worst intention, will never cease. The web hosting, Internet Service Provider, phone companies should extend their best cooperation as well to facilitate efficient investigation in this regard.
More importantly, what the hackers should realize that just because they were not caught now, does not mean they are already off the hook. What they are only doing is accumulate offenses. One day, the hand of the law will reach them. Once that happens, all of these offenses can be combined into a one big case that can put them to jail longer than they think. Even if the owners of the sites that they were able to hack decide not to pursue a case against them, it does not mean they no longer have a liability. The hacking/cracking/piracy provision of the E-Commerce Law makes such acts as criminal offenses in nature, therefore what can only be waived, should the companies decide not to sue them, is the civil liability (monetary damages) and the criminal liability will still be pursued by the state.
I hope that publications can play a role in sparking vigilance among Internet users of this country and the world against acts of hacking/cracking/piracy. The act of hacking should never be glamorized and even make these people who commits these acts as heroes. It may send a wrong signal that our younger Internet generation might misunderstand.
These people are seeing that they're getting the media mileage and attention that they long for and see it like a merit/badge of their hacking accomplishment. Being published, talked about, is I'm very sure, a big deal for some of these guys.
I hope to see the computer publications as a medium in making the Internet users vigilant and not scared/wary of these hackers. Perhaps feature articles on how the NBI, ISPs, phone companies, National Security Council, handle these incidents.
Hacking, cracking, piracy is a crime under RA8792. The iron hand of the law must be fully enforced or else this can propagate further and cause irreparable damage to the Philippine Internet industry as a whole. The increase number of hacking incidents these past few weeks is already alarming. Worst, these people seems to be enjoying it and not even bothered with the consequences.
Biyernes, Abril 15, 2011
CARAGA
CARAGA
From WikiPilipinas: The Hip 'n Free Philippine Encyclopedia
Jump to: navigation, search
 | |
| Regional center | Butuan City |
|---|---|
| Population | 2,803,805 |
| – Density | 148.8 per km² |
| Area | 18,847.7 km² |
| Divisions | |
| – Provinces | 5 |
| – Cities | 3 |
| – Municipalities | 70 |
| – Barangays | 1,310 |
| – Cong. districts | 7 |
| Languages | Surigaonon, Cebuano, Butuanon, Manobo, others |
- For the municipality in the province of Davao Oriental, see Caraga, Davao Oriental
[edit] History
The history of Caraga can be traced back to the 15th century when explorers discovered the existence of "Kalagans", believed to be of Visayan Origin in one of the three districts in Mindanao. The word Caraga originated from the Visayan word Kalagan: kalag meaning soul or people, and an meaning land. The Kalagans have a long history of being brave and fearless. Thus, the region was called by early chroniclers as the "Land of the Brave and Fierce People".The "Kalagans", called "Caragans" by the Spaniards, occupied the district composed of the two provinces of Surigao, the northern part of Davao Oriental and eastern Misamis Oriental. The two Agusan Provinces were later organized under the administrative jurisdiction of Surigao and became the independent Agusan province in 1914. In 1960, Surigao was divided into Norte and Sur, and in June 1967, Agusan followed suit. While Butuan then was just a town of Agusan, the logging boom in the 1950s drew business to the area. On August 2 1950, by virtue of Republic Act 523, the City Charter of Butuan was approved.
It is reported that during the early years of the Caraga region, its inhabitants came from mainland Asia, followed by Malayans, Arabs, Chinese, Japanese, Spanish and Americans. Migrants from the Visayan and Luzon provinces later settled in the area. Most of its inhabitants speak the Cebuano dialect and reside in the rural areas.
CLIMATE The region in general has no definite dry season. Rainfall occurs throughout the year with heavy rains from November to January.
NATURAL RESOURCES Rich in natural resources, the region has large tracts of land available for development. The region is noted for its wood based economy, its extensive water resources and its rich mineral deposits such as iron, gold, silver, nickel, chromite, manganese and copper. Its leading crops are palay, banana and coconut.
It has excellent tourism potentials because of its unspoiled and beautiful beaches, abundant and fresh seafood, ancient and historical landmarks, hot and cold springs, evergreen forests.
[edit] Political divisions
Caraga is subdivided into 5 provinces and Butuan City.| Province/City | Capital | Population (2000) | Area (km²) | Pop. density (per km²) | |
|---|---|---|---|---|---|
 | Agusan del Norte | Cabadbaran | 285,570 | 1,773.2 | 161.0 |
 | Agusan del Sur | Prosperidad | 559,294 | ||
Teaching Principles
Teaching is a complex, multifaceted activity, often requiring us as instructors to juggle multiple tasks and goals simultaneously and flexibly. The following small but powerful set of principles can make teaching both more effective and more efficient, by helping us create the conditions that support student learning and minimize the need for revising materials, content, and policies. While implementing these principles requires a commitment in time and effort, it often saves time and energy later on.Effective teaching involves acquiring relevant knowledge about students and using that knowledge to inform our course design and classroom teaching.
When we teach, we do not just teach the content, we teach students the content. A variety of student characteristics can affect learning. For example, students’ cultural and generational backgrounds influence how they see the world; disciplinary backgrounds lead students to approach problems in different ways; and students’ prior knowledge (both accurate and inaccurate aspects) shapes new learning. Although we cannot adequately measure all of these characteristics, gathering the most relevant information as early as possible in course planning and continuing to do so during the semester can (a) inform course design (e.g., decisions about objectives, pacing, examples, format), (b) help explain student difficulties (e.g., identification of common misconceptions), and (c) guide instructional adaptations (e.g., recognition of the need for additional practice).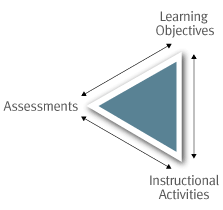
Effective teaching involves aligning the three major components of instruction: learning objectives, assessments, and instructional activities.
Taking the time to do this upfront saves time in the end and leads to a better course. Teaching is more effective and student learning is enhanced when (a) we, as instructors, articulate a clear set of learning objectives (i.e., the knowledge and skills that we expect students to demonstrate by the end of a course); (b) the instructional activities (e.g., case studies, labs, discussions, readings) support these learning objectives by providing goal-oriented practice; and (c) the assessments (e.g., tests, papers, problem sets, performances) provide opportunities for students to demonstrate and practice the knowledge and skills articulated in the objectives, and for instructors to offer targeted feedback that can guide further learning.Effective teaching involves articulating explicit expectations regarding learning objectives and policies.
There is amazing variation in what is expected of students across American classrooms and even within a given discipline. For example, what constitutes evidence may differ greatly across courses; what is permissible collaboration in one course could be considered cheating in another. As a result, students’ expectations may not match ours. Thus, being clear about our expectations and communicating them explicitly helps students learn more and perform better. Articulating our learning objectives (i.e., the knowledge and skills that we expect students to demonstrate by the end of a course) gives students a clear target to aim for and enables them to monitor their progress along the way. Similarly, being explicit about course policies (e.g., on class participation, laptop use, and late assignment) in the syllabus and in class allows us to resolve differences early and tends to reduce conflicts and tensions that may arise. Altogether, being explicit leads to a more productive learning environment for all students. More information on how clear learning objectives supports students' learning. (pdf)Effective teaching involves prioritizing the knowledge and skills we choose to focus on.
Coverage is the enemy: Don’t try to do too much in a single course. Too many topics work against student learning, so it is necessary for us to make decisions – sometimes difficult ones – about what we will and will not include in a course. This involves (a) recognizing the parameters of the course (e.g., class size, students’ backgrounds and experiences, course position in the curriculum sequence, number of course units), (b) setting our priorities for student learning, and (c) determining a set of objectives that can be reasonably accomplished.Effective teaching involves recognizing and overcoming our expert blind spots.
We are not our students! As experts, we tend to access and apply knowledge automatically and unconsciously (e.g., make connections, draw on relevant bodies of knowledge, and choose appropriate strategies) and so we often skip or combine critical steps when we teach. Students, on the other hand, don’t yet have sufficient background and experience to make these leaps and can become confused, draw incorrect conclusions, or fail to develop important skills. They need instructors to break tasks into component steps, explain connections explicitly, and model processes in detail. Though it is difficult for experts to do this, we need to identify and explicitly communicate to students the knowledge and skills we take for granted, so that students can see expert thinking in action and practice applying it themselves.Effective teaching involves adopting appropriate teaching roles to support our learning goals.
Even though students are ultimately responsible for their own learning, the roles we assume as instructors are critical in guiding students’ thinking and behavior. We can take on a variety of roles in our teaching (e.g., synthesizer, moderator, challenger, commentator). These roles should be chosen in service of the learning objectives and in support of the instructional activities. For example, if the objective is for students to be able to analyze arguments from a case or written text, the most productive instructor role might be to frame, guide and moderate a discussion. If the objective is to help students learn to defend their positions or creative choices as they present their work, our role might be to challenge them to explain their decisions and consider alternative perspectives. Such roles may be constant or variable across the semester depending on the learning objectives.Effective teaching involves progressively refining our courses based on reflection and feedback.
Teaching requires adapting. We need to continually reflect on our teaching and be ready to make changes when appropriate (e.g., something is not working, we want to try something new, the student population has changed, or there are emerging issues in our fields). Knowing what and how to change requires us to examine relevant information on our own teaching effectiveness. Much of this information already exists (e.g., student work, previous semesters’ course evaluations, dynamics of class participation), or we may need to seek additional feedback with help from the university teaching center (e.g., interpreting early course evaluations, conducting focus groups, designing pre- and posttests). Based on such data, we might modify the learning objectives, content, structure, or format of a course, or otherwise adjust our teaching. Small, purposeful changes driven by feedback and our priorities are most likely to be manageable and effective.
- Enhancing Education
- http://www.cmu.edu/teaching/
- Eberly: (412) 268-2896 | OTE: (412) 268-5503 | Blackboard: (412) 268-9090
Mag-subscribe sa:
Mga Komento (Atom)


